By Sandro Pinto, Head of Research and Development at Hex Five Security Inc.
The Internet of Things, also known as the IoT, refers to the billions of physical devices around the world that are now connected to the internet, all collecting and sharing vast amounts of data. Due to the sheer amount of connected devices, the IoT has become an integral part of the lives of billions of people around the world and many believe that the IoT is the most important development of the 21st century as it impacts almost every industry, from healthcare to transportation. However, as the world around us becomes more and more connected, securing these resource-constrained devices has become paramount to say the least. One avenue to securing the IoT is to leverage a layered security approach that utilizes a Trusted Execution Environment (TEE) to shield critical functionality from untrusted software components and well-established cryptographic methods to protect data in transit and at rest. The security of most IoT devices is flawed at its core as limited hardware capabilities leads to the development of monolithic firmware. MCU-based devices typically do not provide a means of separation between trusted and untrusted software components. Third-party binaries, open source libraries, legacy code, applications, drivers and the operating system share access to the same hardware resources as they run at the same privilege level. Security can only be as strong as the weakest link in the chain: exploiting a single vulnerability in any components of the monolithic firmware is enough to compromise the entire device. A TEE is necessary to guarantee a device or system’s data and programs confidentiality, integrity and availability (CIA). Traditional TEE technology which has the ability to “carve-out” one safe area across the various hardware components – commonly referred as the “secure world” – has been available in the market for some time. However, this specific TEE technology has never achieved widespread adoption outside the mobile market because of two major drawbacks. First, the underlying hardware blocks are based on proprietary IP leading to expensive, fragmented implementations across vendors and platforms. Second, the hardware-centric approach typical of a silicon IP provider results in overly complex and rigid software implementations, which is very difficult to understand, and even more difficult to properly implement across different microarchitectures. In addition, over the last few years confidence in this hardware-heavy approach has been shaken due to the systematic discovery of critical vulnerabilities in the microarchitectural components. The RISC-V instruction set architecture’s (ISA) clean slate design overcomes these limitations as it defines most of the TEE hardware requirements as part of the standard specs. This makes the TEE hardware blocks available out of the box in any RISC-V implementation without the need for proprietary IP. These hardware blocks include privileged execution extensions and the physical memory protection (PMP) primitive. The open design of these RISC-V primitives makes the ISA’s TEE implementation very scalable across silicon implementations from tiny 32-bit single core MCUs to 64-bit multicore Linux capable systems. As a step towards real-world IoT applications, Hex Five Security – a long-time member of RISC-V International – has developed MultiZone Security IoT Stack, a free to download secure IoT stack for RISC-V. Hex Five’s MultiZone Security TEE orchestrates the underlying RISC-V hardware security blocks and provides hardware-enforced, software-defined separation across multiple equally secure, lightweight threads mapped to hardware resources called “zones.” The programs running in zones are intrinsically secure as they are executed in unprivileged user mode. Access to hardware resources – ram/rom/peripherals – not explicitly mapped to a zone is prevented by the RISC-V physical memory protection (PMP) unit that triggers a fault. In addition to the MultiZone TEE, the Hex Five Secure IoT Stack includes three other open source components: FreeRTOS, the WolfSSL crypto library, and the picoTCP IP stack. The application is comprised of four separated zones defined via static policies. Each zone is physically separated and shares no hardware resources with the other zones and with the MultiZone runtime; each zone is sealed and provides a safety-critical real-time scheduler and a secure communications layer.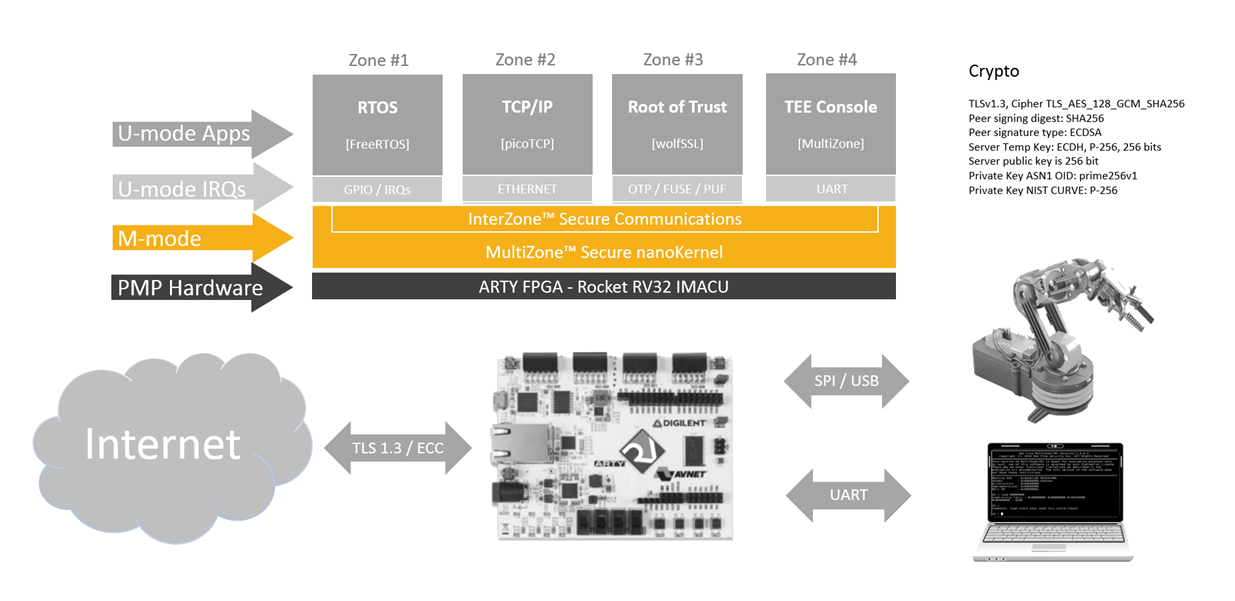 1. Zone one runs FreeRTOS and its three tasks include: a CLI application providing a user console, a real-time application controlling the movements of a robotic arm, and a heartbeat application showing a separate real time thread managing button interrupts and LEDs.
2. Zone two runs the TCP/IP stack providing TLS 1.3 connectivity to the cloud. This isolates the remote attack surface from the real time operating system and from the Root of Trust.
3. Zone three runs the Root of Trust and the WolfSSL library. It provides the cryptographic key required to secure the TLS link. Secrets (encryption keys, passwords, protected files, etc.) never leave this zone and can only be accessed via MultiZone secure messages.
4. Zone four runs a bare metal UART terminal to verify the enforcement of the separation policies and to measure the performance of the MultiZone TEE.
To enable communications between the otherwise isolated zones, their APIs are wrapped in request / response messages routed via the secure communications infrastructure provided by the TEE. This technique allows quick and robust integration with third-party software functionality now exposed as micro-services.
Embedded applications require a layered security approach. Security through separation is essential, as it shields critical functionality from the attack surface introduced by untrusted large code base software. The days of proprietary, overly complicated, hardware-heavy TEEs are over as this legacy approach has proven inadequate to meet cost and agility requirements of modern IoT applications. Hex Five’s MultiZone Security offers a quick and safe way to add security and separation to RISC-V applications. MultiZone is based on RISC-V standards and can retrofit existing designs: you can take advantage of high security separation without the need for hardware and software redesign, eliminating the complexity associated with managing a hybrid hardware/software security scheme.
For more information about MultiZone Security visit: http://hex-five.com.
1. Zone one runs FreeRTOS and its three tasks include: a CLI application providing a user console, a real-time application controlling the movements of a robotic arm, and a heartbeat application showing a separate real time thread managing button interrupts and LEDs.
2. Zone two runs the TCP/IP stack providing TLS 1.3 connectivity to the cloud. This isolates the remote attack surface from the real time operating system and from the Root of Trust.
3. Zone three runs the Root of Trust and the WolfSSL library. It provides the cryptographic key required to secure the TLS link. Secrets (encryption keys, passwords, protected files, etc.) never leave this zone and can only be accessed via MultiZone secure messages.
4. Zone four runs a bare metal UART terminal to verify the enforcement of the separation policies and to measure the performance of the MultiZone TEE.
To enable communications between the otherwise isolated zones, their APIs are wrapped in request / response messages routed via the secure communications infrastructure provided by the TEE. This technique allows quick and robust integration with third-party software functionality now exposed as micro-services.
Embedded applications require a layered security approach. Security through separation is essential, as it shields critical functionality from the attack surface introduced by untrusted large code base software. The days of proprietary, overly complicated, hardware-heavy TEEs are over as this legacy approach has proven inadequate to meet cost and agility requirements of modern IoT applications. Hex Five’s MultiZone Security offers a quick and safe way to add security and separation to RISC-V applications. MultiZone is based on RISC-V standards and can retrofit existing designs: you can take advantage of high security separation without the need for hardware and software redesign, eliminating the complexity associated with managing a hybrid hardware/software security scheme.
For more information about MultiZone Security visit: http://hex-five.com.
About the Author
 Sandro Pinto is Head of Research and Development at Hex Five Security Inc. and a Research Scientist and Professor at the University of Minho, Portugal. Sandro is a hardware security wizard, world-class expert in Trusted Execution Environment technology and a prolific writer of security-oriented research papers. Sandro holds a Ph.D. in Electronics and Computer Engineering and has a deep academic background and several years of industry experience focusing on operating systems, virtualization, and security for embedded, cyber-physical and IoT-based systems.]]>
Sandro Pinto is Head of Research and Development at Hex Five Security Inc. and a Research Scientist and Professor at the University of Minho, Portugal. Sandro is a hardware security wizard, world-class expert in Trusted Execution Environment technology and a prolific writer of security-oriented research papers. Sandro holds a Ph.D. in Electronics and Computer Engineering and has a deep academic background and several years of industry experience focusing on operating systems, virtualization, and security for embedded, cyber-physical and IoT-based systems.]]>


