This blog was submitted by Silex Insight.
If you are designing systems based on a RISC-V architecture, for example to run highly connected applications, you want to include tight, future-proof security. Both for your customers’ experience and your reputation, you want to avoid a breach of security – leaking private data or even changing the functionality. Therefore, security should be part of the fabric of your system. Luckily, the RISC-V architecture offers a solid ground for security. In addition, there are several companies that have designed ready-made IP blocks that you can integrate with RISC-V designs.
Security should be taken into account from the very first design notes, not as an afterthought to be added with a few drops of software.
What makes RISC-V so appealing?

RISC-V is an instruction set architecture (ISA) based on established principles for reduced instruction set computers (RISC). Unlike most other ISA designs, the RISC-V ISA is provided under free, open-source licenses. Lately, it is gaining traction and a fast-growing number of companies have announced or started offering RISC-V hardware.
The appeal of RISC-V is clear: in contrast to alternative architectures from leading vendors, it supports building innovative, specialized microprocessor designs. It is flexible and modular and so it bypasses one-size-fits-all designs full of prepackaged features and capabilities that you may not need, but that cost your applications dearly in terms of performance and energy usage. In comparison to proprietary RISC and its open-source nature, RISC-V combines its high level of flexibility with a much lower cost.
No wonder it attracts a growing number of companies that want to produce custom chips. Such RISC-V chips are eventually also expected to appear in traditional computing. Their real added value, however, will be in driving the connected applications that make up the Internet of Things (IoT) and the Industrial IoT (IIoT), applications that include home appliances and wearables, medical devices and implantables, robotics and automated factory equipment, and also autonomous vehicles.
A glaring issue for embedded IoT/IIoT systems: security
If we have learned anything from the recent history of connected devices, it is their vulnerability to all types of accidental and malicious misuse.
For even sensitive applications as heart implants, car key fobs, or nuclear power plant equipment have proven to be vulnerable. High-volume applications such as household appliances, camera image sensors, or even hard disk controllers form an especially attractive attack surface for hackers.
All these examples readily show the importance of safeguarding the authenticity, confidentiality, and integrity of applications running on your chips.
Not doing so may cause damage, or in some cases, even physical incidents. Furthermore, intellectual property might be copied, leaked, or compromised, causing a loss of competitive advantage. All this can result in litigation cases, compensation fees, and ultimately, damage to your reputation and bottom line.
Why software alone is not up to the task
The required level of security for a processor depends on many factors that may often only become clear once it is up and running.
- What is the physical access to the device (public or in-company)?
- Can a breach of the device be isolated, or will it affect other devices?
- Will privacy-related, sensitive, regulated data be harvested, stored, or transferred?
- Are the application or its data attractive targets for someone?
- Which firmware or software will run on the processor?
Depending on software alone to protect a processor and its applications may not be the best idea. Software is most often the layer that is added last, and the temptation looms large to delay all decisions about security to the moment the processor is ready. That, however, resembles building a house without solid walls and locks and then depending on written warnings to deter intruders.
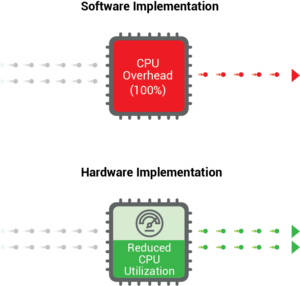
Also, if the cryptography is to be entirely run in software and there is frequent authentication and moderate to heavy cryptography, the processor may be loaded up to 80-100% with the necessary calculations at a given time.
This may seriously downgrade the performance of the applications, halting them altogether at times. Also, software cryptography may leak more critical information, making it easier for hackers to stage successful attacks. Even with direct information unavailable, software operations are still more prone to side-channel attacks.
Therefore, it is wiser to implement security in the hardware and to consider doing so from the get-go. Such a secure and efficient solution requires a well-thought-out process. This process involves starting the security analysis at the very beginning of the development cycle before any specific development or coding has begun. A process that also considers all issues such as how to store keys, securely update a device, debug securely, and repair without security risks.
Security in hardware, relieving you from security headaches
RISC-V has a native set of solid security mechanisms, including 4-ring trust, secure interrupt processing, and a mechanism for physical memory protection (PMP). To add to that, many companies have released solutions in the form of extensions and hardware IP blocks. These include cryptographic libraries, roots of trust, and security vaults. They can be taken into account and added early on in the design process and relieve you of security headaches.
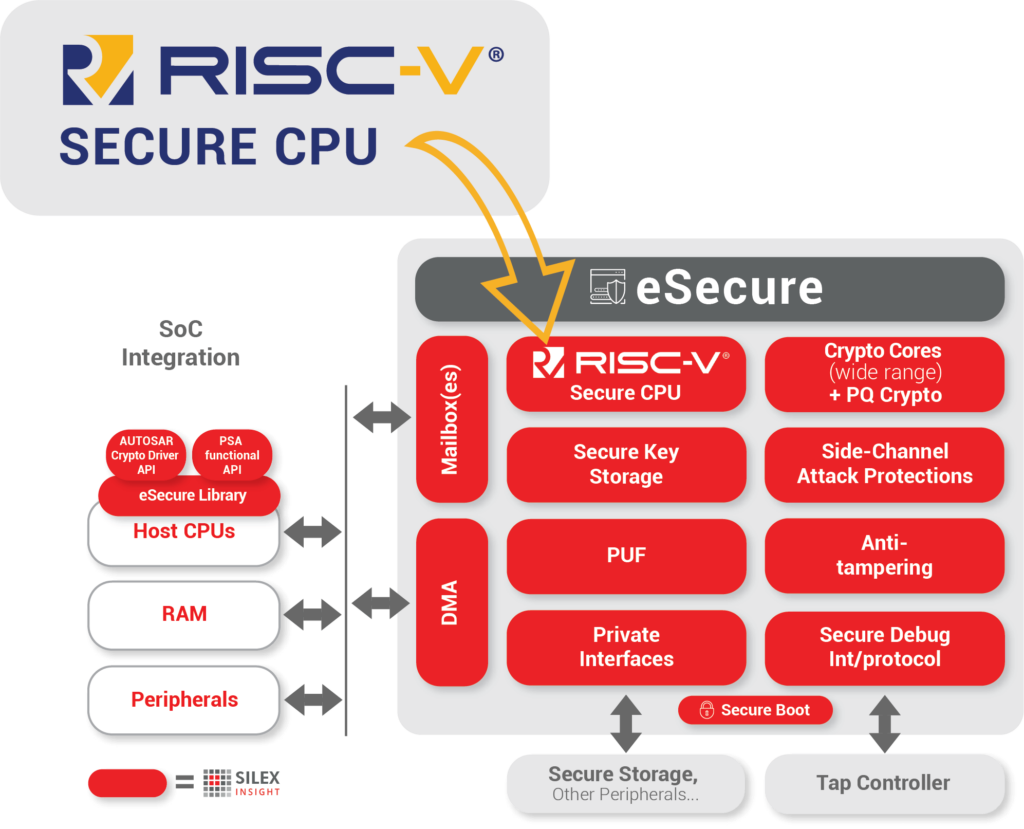
Ideally a comprehensive solution should be included, such as a true security vault and root-of-trust core. This will then serve as the basis to secure almost all applications including IoT, edge sensors, storage devices, or communication.
One example of a complete solution sets up a separate RISC-V secure CPU. It should include secure APIs for the host secure storage, peripherals, RAM, etc., which can call on its authentication and cryptographic services without ever getting access to the system’s secrets.
Features to be included
- DEVICE UNIQUE IDENTITY: For each device, a key may be generated based on the unique properties of the underlying hardware. Such physical unclonable functions (PUFs) are the device’s unique, unforgeable fingerprint.
- SECURE BOOT: A secure boot process ensures that only correct, unaltered software is run.
- SECURE STORAGE: The keys can be stored securely, in hardware, and will not leave the module.
- SIDE-CHANNEL ATTACK PROTECTION: A protection against side-channel attacks, where the perpetrators would try to exploit the physical properties of the system such as energy usage to deduce the system’s secrets and gain access.
- ANTI-TAMPERING: Attempts to tamper with the device will be detected and logged.
- WIDE VARIETY OF CRYPTOGRAPHIC FUNCTIONS: A mechanism to securely offload authentication and encryption functionality to support the latest standards and algorithms, including, for example, those that are required on the Chinese market.
- SECURE DEBUGGING AND OTA UPDATES: A mechanism for secure debugging and updating (OTA, Over the Air).
The algorithms should come with several highly trustworthy certifications. All relevant algorithms should have a NIST CAVP certification; minimum FIPS 140-2 level 3. For the payment card industry, the solution should be PCI DSS certified. In addition, it should be OSCCA certified for the Chinese market, and also effectively be engineered into automotive HSM solutions (ISO 26262).
To cater to a variety of customers, use cases, and applications, the module that you should use, should be highly configurable and offer a variety of options in terms of security functions, performance, area, and power consumption. As a result, it can be fit precisely to your needs, resulting in the best trade-off and lowest production cost.
Let’s make RISC-V processors synonymous with security
Processors based on RISC-V are projected to assume a growing share of the connected IoT and IIoT markets. However, they can only do so if they provide tight security to guard the confidentiality and integrity of applications and data.
Hardware IP blocks form an efficient and elegant way to provide that security. With these solutions, system integrators and application builders can design a trusted, secure processor that relieves them of much of the security headache and makes their applications ready for even the most demanding and regulated environments.
About Silex Insight
Silex Insight is a recognized market-leading independent supplier of Security IP solutions for embedded systems and custom OEM solutions for AVoIP/Video IP codec. The security platforms and solutions from Silex Insight include flexible and high-performance crypto-engines which are easy to integrate and an eSecure IP module that provides a complete security solution for all platforms. For custom OEM solutions for AVoIP/Video IP codec, Silex Insight provides high-end image and video compression solutions for distributing low latency, 4K HDR video over IP. Development takes place at the headquarters near Brussels, Belgium.
For more information: