Introduction
Among many new things in the 21st century, internet and IoT have been one of the most significant human advancements. As fast-paced and accelerating as they evolve, needs for the number of connected devices are increasing substantially as a result. The “Internet of Everything” has become the new future global networks. While the explosive growth of mobile platform usage have enabled successful business transactions, various concerns of security breach arise inevitably. Most applications are not protected completely. Therefore, individuals and businesses are faced with privacy abuse and data loss.
Device chips must have Trusted Execution Environments (TEEs) in order to protect system programs, device parameters, security user information. TEEs have been widely recognized as the standard environment in mobile devices, payment, Digital Rights Management (DRM), automotive, unmanned aerial vehicle (UAV), and IoT industries. Currently, the available technologies for implementing TEEs include ARM’s TrustZone, Intel’s Software Guard Extensions (SGX), and AMD’s Secure Encrypted Virtualization (SEV).
This article will describe the security extensions for RISC-V-based XuanTie C series processors, which are developed based on RISC-V’s physical memory protection (PMP) mechanism and privileged architecture. Multiple mutually isolated and executable virtualized zones are created to form TEEs in RISC-V architecture. The purpose of this design is to protect software, memory, peripherals, and I/O within the zones from outside intrusions. Furthermore, processor resources, such as cache, interrupt, memory, and code execution, are isolated so that processors can be run in different zones at the same time.
Security extensions of the RISC-V architecture
Traditional RISC-V processors do not have isolation technologies like ARM TrustZone. RISC-V processors run in Rich Execution Environments (REEs), as shown in Figure 1.
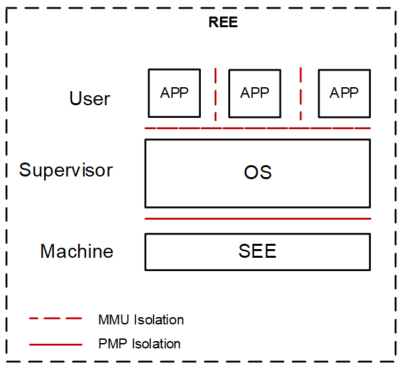
Figure 1: RISC-V privilege architecture
In Fact, RISC-V offers two security mechanisms: PMP and machine mode (M-mode). PMP is a feature that partitions a processor’s physical memory into multiple arbitrarily sized memory regions and defines different access permissions for these regions. It can also separate environments running in supervisor mode (S-mode) from each other, which will be described in details in the subsequent sections. In addition, ARM has the equivalent of RISC-V PMP, MPU, which is only supported in Cortex-M architecture. The second security mechanism is machine mode(M-mode). It has the highest privileges, similarly in monitor mode in ARM. M-mode can manage the execution of multiple environments in S-mode and interfere interrupts and exceptions from any environment in S-mode or user-mode (U-mode). With PMP and M-mode, environments running in S-mode can be isolated from each other. Environments can be managed by a higher privilege level.
Security extension of XuanTie C series processors
Despite the fact that RISC-V processors have incorporated PMP, privileged architecture, and memory management units (MMUs) to achieve TEEs, processors must be built to support other security specifications for fully secure execution environments. To meet the isolation requirements of TEEs, XuanTie C-series processors are equipped with extended security features based on the RISC-V architecture. As a result, multiple virtualized execution zones with unique identifiers are created with the coordination from the software running in M-mode. As illustrated in Figure 2, each zone contains an independent operating system and some applications. The operating system runs in S-mode, whereas the applications run in U-mode. The processors can switch between different zones as required. When this happens, the processors occupy the entire physical core in real-time, and the zone ID will also be updated to that of the corresponding virtualized execution zone. Such zone switching is performed by a Trusted Firmware (TF) running in the highest privilege mode (i.e. M-mode).
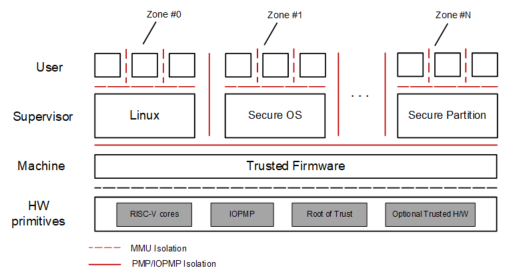
Figure 2: RISC-V system architecture after zone extension
Zone access and isolation in between are achieved by the real-time switching of PMP.
Physical Memory Protection (PMP)
An optional physical memory protection (PMP) unit provides per-hart machine-mode control registers to allow physical memory access privileges (read, write, execute) to be specified for each physical memory region. It is used to isolate physical address access in M-mode from others. PMP also protects the L1/L2 caches.
One of the limitations of PMP is that it is only available in M-mode. PMP consists of multiple (typically8 to 16) groups of address and configuration registers, which can be used to grant or revoke executable, writable, readable (XWR) permissions in S/U-mode. At the same time, PMP protects memory-mapped I/O (MMIO). It is also necessary to configure PMP unit for TF in M-mode in order to limit CPU access to device I/O resources.
PMP configuration is also useful when switching hardware thread between zones is necessary. TF in M-mode allows for design of the current zone to be saved, which then permits the loading of PMP configuration to the next zone. This way, the switching of memory and MMIO access permissions is properly and successfully implemented.
PMP has granted other important features such as memory sharing among multiple zones at the same time. Access permissions of the required memory will be written to the PMP configuration table of each zone, following by being updated by TF upon zone switching. Figure 3 shows a conventional PMP configuration of multiple zones. SHM indicates the shared memory space accessible to the zones.
Another highlighted feature is that PMP can reinforce strict permissions on M-mode of specific memory region, hence reducing exposure to attacks on M-mode. This is also known as Supervisor Memory Access Prevention (SMAP) and Supervisor Memory Execution Prevention (SMEP).
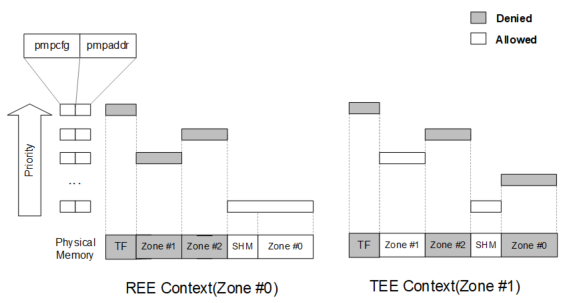
Figure 3: PMP configuration in different zones
IOPMP
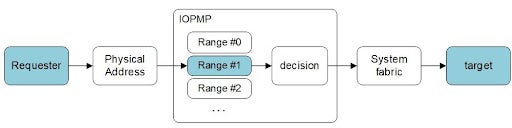
While the RISC-V CPU may have PMP to control its accesses, a mechanism is also needed to control accesses from other bus masters.
In this case, the IOPMP unit is required. IOPMP and PMP shares the same definition on access permissions IOPMP checks for access requests from the bus or master device. Only valid inquiries can be further transferred to the target device. There are three ways to mount IOPMO units:
- IOPMP unit mounted to the requesting client
Each IOPMP unit is independent and is required for each master device. This design is simple and flexible, however, IOPMP units cannot be shared across master devices, as shown in the following figure.
- IOPMP unit mounted to the target client
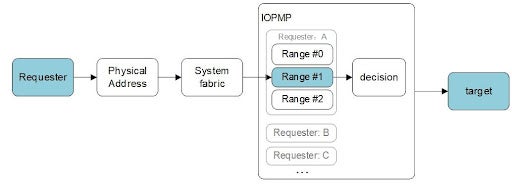
The IOPMP unit on the target client distinguishes between access requests from different master devices. This design requires a master ID from each device, as demonstrated in the following figure.
- Cascaded IOPMP unit on the requesting and target clients
In complex SoC systems, IOPMP units are often cascaded. A common scenario is that the RISC-core has a PMP unit. The processor does not require filtering RISC-core access on the target client. The typical solution is to remove the constraint on CPU access in the table entry of IOPMP. However, this will occupy the IOPMP table entry and lower efficiency. One remedy is that upon the units being cascaded, IOPMP needs to provide a mechanism for pass-through access to some master devices (i.e. providing a configurable list of master devices).
The following figure shows the diagram of a secure SoC system built by using PMP and IOPMP.
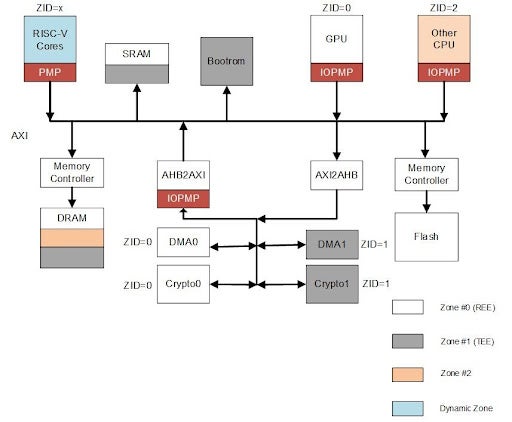
Conclusion
This article describes security capabilities provided by the RISC-V architecture to implement TEEs. Based on the RISC-V’s PMP, privileged architecture, and memory management unit, T-Head XuanTie processors extend some security features to achieve TEEs based on zone management. This solution does not require virtualization support. It requires the capability if implementing multiple TEEs with the support of three privilege modes (U-mode, S-mode, and M-mode), as well as TF management.
TFs running in M-mode need to save and switch contexts with different zone transitions. Although this may result in resource consumption, virtualization technologies, such as ARM TrustZone, also require the switching between the normal and the secure world. The world switching task is performed in hidden mode by TF which runs in M-mode. The difference is that ARM TrustZone partitions two virtualized worlds, whereas extended XuanTie RISC-V processors can simultaneously support 16 zones at most. This solution opens more possibilities for future software security solutions.
For more details, see https://occ.t-head.cn/en